In the last article about FreeRadius (Here), I wrote about basic settings and now I’ll write something about inserting users into database (MySQL).
The FreeRadius database schema contains several tables:
nas
This table contains data about NASes (radius clients) and it is a “replacement” for clients.conf file. It is much easier to maintain the clients in the database than inside config file. If you want to use database for NAS list, skip the step in the last howto (the part about clients.conf). Also, in case you want to keep your NASes in the nas table, you’ll need to uncomment the readclients = yes inside sql.conf.
# Set to 'yes' to read radius clients from the database ('nas' table)
# Clients will ONLY be read on server startup. For performance
# and security reasons, finding clients via SQL queries CANNOT
# be done "live" while the server is running.
#
readclients = yes |
As you can see from the comment, you will need to restart radiusd process to allow/disallow specific NAS.
nas table schema is located inside raddb/sql/mysql/nas.sql
To add IP 192.168.0.15 inside nas table, exec next query:
INSERT INTO nas VALUES (NULL , '192.168.0.15', 'myNAS', 'other', NULL , 'mysecret', NULL , NULL , 'RADIUS Client' ); |
and you will have
mysql> select * from nas; +----+--------------+-----------+-------+-------+----------+--------+-----------+---------------+ | id | nasname | shortname | type | ports | secret | server | community | description | +----+--------------+-----------+-------+-------+----------+--------+-----------+---------------+ | 1 | 192.168.0.15 | myNAS | other | NULL | mysecret | NULL | NULL | RADIUS Client | +----+--------------+-----------+-------+-------+----------+--------+-----------+---------------+ 1 row in set (0.00 sec) |
radacct
This table is used for accounting data. In case you want to collect traffic stats, you will need to uncomment sql inside accounting {} section in /usr/local/etc/raddb/sites-available/default. The same table can be used for simultaneous use checking which is faster than radutmp. All you need to do is to uncomment sql inside session {} section inside /usr/local/etc/raddb/sites-available/default and uncomment simul_count_query inside /usr/local/etc/raddb/sql/mysql/dialup.conf
radcheck
This table keeps the check attributes for users (User-Password, Cleartext-Password, Expiration, Simultaneous-Use, Auth-Type, …)
radreply
Is used for reply attributes for specific user. For example Framed-IP-Address, upload and download speed, etc…
radgroupcheck
This table keeps the check attributes for groups (which means, all users inside specific group will be checked against this attributes).
radgroupreply
The same like radreply but for groups. (all users in specific group will get the same speed, etc). Also, Framed-Pool attribute goes here.
radpostauth
This table is used for logging failed login attempts. To use this, you’ll need to uncomment sql inside postauth section (/usr/local/etc/raddb/sites-available/default.). Think twice before you enable this option because it can overload your server with constant inserts. Your customers will probably spend their money on wireless or wired routers so the logging attempts will come over and over.
radusergroup
This table keeps relation between username and specific group and group priority. In Freeradius 1.x this table was named “usergroup” so in case you have your own billing which is made for old schema, rename this table to usergroup
# Table to keep group info
usergroup_table = "radusergroup" |
Examples
We will create a sample service with the next attributes:
– 512kbps download speed
– 128kbps upload speed
– we will use PPPoE – Point to Point Protocol Over Ethernet
– we will assign dynamic IP addresses to our clients from “internet” IP pool
INSERT INTO `radgroupreply` (`id` ,`groupname` ,`attribute` ,`op` ,`value` ) VALUES (NULL , 'testservice', 'Ascend-Xmit-Rate', ':=', '524288'), (NULL , 'testservice', 'Ascend-Data-Rate', ':=', '131072'), (NULL , 'testservice', 'Framed-Pool', ':=', 'internet'); |
As you can see the speed is converted to bps.
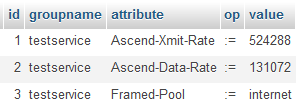
After you created the service, lets create a sample user (assigned with created service).
As I noticed above, check attributes should be placed inside radcheck table.
INSERT INTO `radcheck` (`id` ,`username` ,`attribute` ,`op` ,`value` ) VALUES (NULL , 'testuser', 'User-Password', ':=', 'testpassword'), (NULL , 'testuser', 'Simultaneous-Use', ':=', '1'); |
In this sample, the password is in plain text format which is not reccommended. Insted User-Password (which is alternative to Cleartext-Password for Mikrotik) better option is to use MD5-Password but keep in mind that you won’t be able to use CHAP.
INSERT INTO `radcheck` (`id` ,`username` ,`attribute` ,`op` ,`value` ) VALUES (NULL , 'testuser', 'MD5-Password', ':=', MD5( 'testpassword' ) ), (NULL , 'testuser', 'Simultaneous-Use', ':=', '1'); |
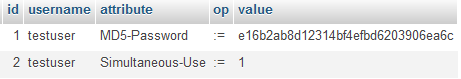
Then we need to assign this user with created service (group)
INSERT INTO `radusergroup` (`username` ,`groupname` ,`priority` ) VALUES ('testuser', 'testservice', '1'); |
![]()
After those inserts, lets test
[root@ns2 raddb]# radtest testuser testpassword 127.0.0.1 0 testing123
Sending Access-Request of id 228 to 127.0.0.1 port 1812
User-Name = "testuser"
User-Password = "testpassword"
NAS-IP-Address = 192.168.0.10
NAS-Port = 0
Message-Authenticator = 0x00000000000000000000000000000000
rad_recv: Access-Accept packet from host 127.0.0.1 port 1812, id=228, length=54
Ascend-Xmit-Rate = 524288
Ascend-Data-Rate = 131072
Framed-Pool = "internet"
[root@ns2 raddb]# |
As you can see, the username/password combination is valid and RADIUS server returned all attributes assigned with user’s group.
To suspend user’s account you can insert Auth-Type := Reject for user.
INSERT INTO `radcheck` (`id` ,`username` ,`attribute` ,`op` ,`value` ) VALUES (NULL , 'testuser', 'Auth-Type', ':=', 'Reject'); |
and we have
[root@ns2 raddb]# radtest testuser testpassword 127.0.0.1 0 testing123 ..... rad_recv: Access-Reject packet from host 127.0.0.1 port 1812, id=145, length=20 |
Another option for disabling users is assigning with specific group which has Auth-Type := Reject inside radgroupcheck
INSERT INTO `radgroupcheck` (`id` ,`groupname` ,`attribute` ,`op` ,`value` ) VALUES (NULL , 'suspended', 'Auth-Type', ':=', 'Reject'); |
Assigning with suspended group can be done with
UPDATE `radusergroup` SET `groupname` = 'suspended' WHERE `username` = 'testuser' AND `priority` = 1; |
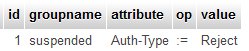
and we have
rad_recv: Access-Reject packet from host 127.0.0.1 port 1812, id=198, length=20 |
Also, keep in mind that routers will try to connect again and again so you will have a big problems in case you have thousands of users. Another option is to assign users with specific group which doesn’t have Auth-Type attribute. Instead rejecting you can assign internal IPs and redirect them to suspended page.
Many questions on FreeRadius mailing list are about Simultaneus-Use. Solution to this problem is very simple and it is very rude to ask this question again and again…
All you need to do is to insert Simultaneous-Use := 1 for specific user (radcheck table) or inside radgroupcheck if you want to limit all users inside specific group.
INSERT INTO `radgroupcheck` (`id` ,`groupname` ,`attribute` ,`op` ,`value` ) VALUES (NULL , 'testservice', 'Simultaneous-Use', ':=', '1'); |
In case you want to set Expiration attribute you can insert the date and the time inside radcheck table.
INSERT INTO `radcheck` (`id` ,`username` ,`attribute` ,`op` ,`value` ) VALUES (NULL , 'testuser', 'Expiration', '==', 'November 30 2011 00:00:00'); |
then we have
[root@ns2 raddb]# radtest testuser testpassword 127.0.0.1 0 testing123
Sending Access-Request of id 28 to 127.0.0.1 port 1812
User-Name = "testuser"
User-Password = "testpassword"
NAS-IP-Address = 192.168.0.10
NAS-Port = 0
Message-Authenticator = 0x00000000000000000000000000000000
rad_recv: Access-Accept packet from host 127.0.0.1 port 1812, id=28, length=60
Ascend-Xmit-Rate = 524288
Ascend-Data-Rate = 131072
Framed-Pool = "internet"
Session-Timeout = 670889 |
You can note Session-Timeout attribute which contains the time in seconds between this moment and the date inside Expiration field. According to this value, the NAS will auto disconnect user when this time expire (in our case 670889 seconds). In case you set the time which already passed (for example yesterdays date) the user will be rejected.
Please keep in mind that this date format works for Mikrotik. I didn’t have chance to test it with other NASes.
If you want to reconnect users at regular intervals (for example every 24 hours – 86400 seconds) you can insert Session-Timeout inside radreply table (because it isn’t check attribute).
To recconect every user inside specific group, add this attribute inside radgroupreply table.
To assign a static IP for specific user insert Framed-IP-Address attribute inside radreply table where Value will be that IP address. Operator should be :=.
Please keep in mind that all inserts inside those tables are visible to radius server right after insert. Only inserts inside nas table won’t be until the restart (service radiusd restart)
I hope this post will help you to set up your own RADIUS server. Also, keep in mind that this is just an example and all this can done in many other ways.
In case you find a spelling errors please contact me so I can fix them.

Hi,
i made configuration for Simultaneous -USe and its the same as yours. I asked a lot of questions in freeradius maillist, thay answered that problem is ME)))
I am weak in freeradius, so i don’t have experience in debuging.
may be, you can help me.
I made configuration for Sim_use=1 in radcheck:
=======================================
mysql> select * from radcheck;
+—-+——————————+——————–+—-+——————————+
| id | username | attribute | op | value |
+—-+——————————+——————–+—-+——————————+
| 11 | user | Cleartext-Password | := | user |
| 3 | test@wimax.com | Cleartext-Password | := | test |
| 15 | KeepAliveUserNameAndPassword | Cleartext-Password | := | KeepAliveUserNameAndPassword |
| 5 | test1@wimax.com | Cleartext-Password | := | test |
| 16 | test@wimax.com | Simultaneous-Use | := | 1 |
| 10 | user | Simultaneous-Use | := | 1 |
| 14 | test1@wimax.com | Framed-Filter-Id | := | SP=data:MSF=data; |
| 13 | test@wimax.com | Framed-Filter-Id | := | SP=data:MSF=data; |
+—-+——————————+——————–+—-+——————————+
8 rows in set (0.00 sec)
=====================================================
As i understood Freeradius has to check radacct for session with acctstoptime IS NULL for Simult users.
but my Freeradius checks /usr/local/var/log/radius/radacct/ …may be the problem is in this??
here is thepartof debug after second user with same username connected:
4) – entering group accounting {…}
(24) detail : expand: %{Packet-Src-IP-Address} -> 10.169.33.11
(24) detail : expand: /usr/local/var/log/radius/radacct/%{%{Packet-Src-IP-Address}:-%{Packet-Src-IPv6-Address}}/detail-%Y%m%d -> /usr/local/var/log/radius/radacct/10.169.33.11/detail-20111214
(24) detail : /usr/local/var/log/radius/radacct/%{%{Packet-Src-IP-Address}:-%{Packet-Src-IPv6-Address}}/detail-%Y%m%d expands to /usr/local/var/log/radius/radacct/10.169.33.11/detail-20111214
(24) detail : expand: %t -> Wed Dec 14 13:57:54 2011
(24) [detail] = ok
can u help me?
thanks
did you removed the comment before sql inside accounting section ? And the same thing before the sql inside session section ?
yse,
freebsd# vi default
######################################################################
#
# As of 2.0.0, FreeRADIUS supports virtual hosts using the
# “server” section, and configuration directives.
#
# Virtual hosts should be put into the “sites-available”
# directory. Soft links should be created in the “sites-enabled”
# directory to these files. This is done in a normal installation.
#
# If you are using 802.1X (EAP) authentication, please see also
# the “inner-tunnel” virtual server. You wll likely have to edit
# that, too, for authentication to work.
#
# $Id$
#
######################################################################
#
# Read “man radiusd” before editing this file. See the section
# titled DEBUGGING. It outlines a method where you can quickly
# obtain the configuration you want, without running into
# trouble. See also “man unlang”, which documents the format
# of this file.
#
# This configuration is designed to work in the widest possible
# set of circumstances, with the widest possible number of
# authentication methods. This means that in general, you should
# need to make very few changes to this file.
#
# The best way to configure the server for your local system
# is to CAREFULLY edit this file. Most attempts to make large
# edits to this file will BREAK THE SERVER. Any edits should
# be small, and tested by running the server with “radiusd -X”.
# Once the edits have been verified to work, save a copy of these
# configuration files somewhere. (e.g. as a “tar” file). Then,
# make more edits, and test, as above.
#
# There are many “commented out” references to modules such
# as ldap, sql, etc. These references serve as place-holders.
# If you need the functionality of that module, then configure
# it in radiusd.conf, and un-comment the references to it in
# this file. In most cases, those small changes will result
# in the server being able to connect to the DB, and to
# authenticate users.
#
######################################################################
#
# In 1.x, the “authorize”, etc. sections were global in
# radiusd.conf. As of 2.0, they SHOULD be in a server section.
#
# The server section with no virtual server name is the “default”
# section. It is used when no server name is specified.
#
# We don’t indent the rest of this file, because doing so
# would make it harder to read.
#
# Authorization. First preprocess (hints and huntgroups files),
# then realms, and finally look in the “users” file.
#
# Any changes made here should also be made to the “inner-tunnel”
# virtual server.
#
# The order of the realm modules will determine the order that
# we try to find a matching realm.
#
# Make *sure* that ‘preprocess’ comes before any realm if you
# need to setup hints for the remote radius server
authorize {
#
# Security settings. Take a User-Name, and do some simple
# checks on it, for spaces and other invalid characters. If
# it looks like the user is trying to play games, reject it.
#
# This should probably be enabled by default.
#
# See policy.conf for the definition of the filter_username policy.
#
# filter_username
#
# The preprocess module takes care of sanitizing some bizarre
# attributes in the request, and turning them into attributes
# which are more standard.
#
# It takes care of processing the ‘raddb/hints’ and the
# ‘raddb/huntgroups’ files.
preprocess
#
# If you want to have a log of authentication requests,
# un-comment the following line, and the ‘detail auth_log’
# section, above.
# auth_log
#
# The chap module will set ‘Auth-Type := CHAP’ if we are
# handling a CHAP request and Auth-Type has not already been set
chap
#
# If the users are logging in with an MS-CHAP-Challenge
# attribute for authentication, the mschap module will find
# the MS-CHAP-Challenge attribute, and add ‘Auth-Type := MS-CHAP’
# to the request, which will cause the server to then use
# the mschap module for authentication.
mschap
#
# If you have a Cisco SIP server authenticating against
# FreeRADIUS, uncomment the following line, and the ‘digest’
# line in the ‘authenticate’ section.
digest
#
# The WiMAX specification says that the Calling-Station-Id
# is 6 octets of the MAC. This definition conflicts with
# RFC 3580, and all common RADIUS practices. Un-commenting
# the “wimax” module here means that it will fix the
# Calling-Station-Id attribute to the normal format as
# specified in RFC 3580 Section 3.21
# wimax
#
# Look for IPASS style ‘realm/’, and if not found, look for
# ‘@realm’, and decide whether or not to proxy, based on
# that.
# IPASS
#
# If you are using multiple kinds of realms, you probably
# want to set “ignore_null = yes” for all of them.
# Otherwise, when the first style of realm doesn’t match,
# the other styles won’t be checked.
#
suffix
# ntdomain
#
# This module takes care of EAP-MD5, EAP-TLS, and EAP-LEAP
# authentication.
#
# It also sets the EAP-Type attribute in the request
# attribute list to the EAP type from the packet.
#
# As of 2.0, the EAP module returns “ok” in the authorize stage
# for TTLS and PEAP. In 1.x, it never returned “ok” here, so
# this change is compatible with older configurations.
#
# The example below uses module failover to avoid querying all
# of the following modules if the EAP module returns “ok”.
# Therefore, your LDAP and/or SQL servers will not be queried
# for the many packets that go back and forth to set up TTLS
# or PEAP. The load on those servers will therefore be reduced.
#
eap {
ok = return
}
#
# Pull crypt’d passwords from /etc/passwd or /etc/shadow,
# using the system API’s to get the password. If you want
# to read /etc/passwd or /etc/shadow directly, see the
# passwd module in radiusd.conf.
#
# unix
#
# Read the ‘users’ file
# files
#
# Look in an SQL database. The schema of the database
# is meant to mirror the “users” file.
#
# See “Authorization Queries” in sql.conf
sql
#
# If you are using /etc/smbpasswd, and are also doing
# mschap authentication, the un-comment this line, and
# configure the ‘etc_smbpasswd’ module, above.
# etc_smbpasswd
#
# The ldap module will set Auth-Type to LDAP if it has not
# already been set
# ldap
#
# Enforce daily limits on time spent logged in.
# daily
#
# Use the checkval module
# checkval
expiration
logintime
#
# If no other module has claimed responsibility for
# authentication, then try to use PAP. This allows the
# other modules listed above to add a “known good” password
# to the request, and to do nothing else. The PAP module
# will then see that password, and use it to do PAP
# authentication.
#
# This module should be listed last, so that the other modules
# get a chance to set Auth-Type for themselves.
#
pap
#
# If “status_server = yes”, then Status-Server messages are passed
# through the following section, and ONLY the following section.
# This permits you to do DB queries, for example. If the modules
# listed here return “fail”, then NO response is sent.
#
# Autz-Type Status-Server {
#
# }
}
# Authentication.
#
#
# This section lists which modules are available for authentication.
# Note that it does NOT mean ‘try each module in order’. It means
# that a module from the ‘authorize’ section adds a configuration
# attribute ‘Auth-Type := FOO’. That authentication type is then
# used to pick the apropriate module from the list below.
#
# In general, you SHOULD NOT set the Auth-Type attribute. The server
# will figure it out on its own, and will do the right thing. The
# most common side effect of erroneously setting the Auth-Type
# attribute is that one authentication method will work, but the
# others will not.
#
# The common reasons to set the Auth-Type attribute by hand
# is to either forcibly reject the user (Auth-Type := Reject),
# or to or forcibly accept the user (Auth-Type := Accept).
#
# Note that Auth-Type := Accept will NOT work with EAP.
#
# Please do not put “unlang” configurations into the “authenticate”
# section. Put them in the “post-auth” section instead. That’s what
# the post-auth section is for.
#
authenticate {
#
# PAP authentication, when a back-end database listed
# in the ‘authorize’ section supplies a password. The
# password can be clear-text, or encrypted.
Auth-Type PAP {
pap
}
#
# Most people want CHAP authentication
# A back-end database listed in the ‘authorize’ section
# MUST supply a CLEAR TEXT password. Encrypted passwords
# won’t work.
Auth-Type CHAP {
chap
}
#
# MSCHAP authentication.
Auth-Type MS-CHAP {
mschap
}
#
# If you have a Cisco SIP server authenticating against
# FreeRADIUS, uncomment the following line, and the ‘digest’
# line in the ‘authorize’ section.
digest
#
# Pluggable Authentication Modules.
# pam
#
# See ‘man getpwent’ for information on how the ‘unix’
# module checks the users password. Note that packets
# containing CHAP-Password attributes CANNOT be authenticated
# against /etc/passwd! See the FAQ for details.
#
# For normal “crypt” authentication, the “pap” module should
# be used instead of the “unix” module. The “unix” module should
# be used for authentication ONLY for compatibility with legacy
# FreeRADIUS configurations.
#
unix
# Uncomment it if you want to use ldap for authentication
#
# Note that this means “check plain-text password against
# the ldap database”, which means that EAP won’t work,
# as it does not supply a plain-text password.
# Auth-Type LDAP {
# ldap
# }
#
# Allow EAP authentication.
eap
#
# The older configurations sent a number of attributes in
# Access-Challenge packets, which wasn’t strictly correct.
# If you want to filter out these attributes, uncomment
# the following lines.
#
# Auth-Type eap {
# eap {
# handled = 1
# }
# if (handled && (Response-Packet-Type == Access-Challenge)) {
# attr_filter.access_challenge.post-auth
# handled # override the “updated” code from attr_filter
# }
# }
}
#
# Pre-accounting. Decide which accounting type to use.
#
preacct {
preprocess
#
# Session start times are *implied* in RADIUS.
# The NAS never sends a “start time”. Instead, it sends
# a start packet, *possibly* with an Acct-Delay-Time.
# The server is supposed to conclude that the start time
# was “Acct-Delay-Time” seconds in the past.
#
# The code below creates an explicit start time, which can
# then be used in other modules. It will be *mostly* correct.
# Any errors are due to the 1-second resolution of RADIUS,
# and the possibility that the time on the NAS may be off.
#
# The start time is: NOW – delay – session_length
#
# update request {
# FreeRADIUS-Acct-Session-Start-Time = “%{expr: %l – %{%{Acct-Session-Time}:-0} – %{%{
Acct-Delay-Time}:-0}}”
# }
#
# Ensure that we have a semi-unique identifier for every
# request, and many NAS boxes are broken.
acct_unique
#
# Look for IPASS-style ‘realm/’, and if not found, look for
# ‘@realm’, and decide whether or not to proxy, based on
# that.
#
# Accounting requests are generally proxied to the same
# home server as authentication requests.
# IPASS
suffix
# ntdomain
#
# Read the ‘acct_users’ file
files
}
#
# Accounting. Log the accounting data.
#
accounting {
#
# Create a ‘detail’ed log of the packets.
# Note that accounting requests which are proxied
# are also logged in the detail file.
detail
# daily
# Update the wtmp file
#
# If you don’t use “radlast”, you can delete this line.
unix
#
# For Simultaneous-Use tracking.
#
# Due to packet losses in the network, the data here
# may be incorrect. There is little we can do about it.
# radutmp
# sradutmp
# Return an address to the IP Pool when we see a stop record.
# main_pool
#
# Log traffic to an SQL database.
#
# See “Accounting queries” in sql.conf
sql
#
# If you receive stop packets with zero session length,
# they will NOT be logged in the database. The SQL module
# will print a message (only in debugging mode), and will
# return “noop”.
#
# You can ignore these packets by uncommenting the following
# three lines. Otherwise, the server will not respond to the
# accounting request, and the NAS will retransmit.
#
# if (noop) {
# ok
# }
#
# Instead of sending the query to the SQL server,
# write it into a log file.
#
sql_log
# Cisco VoIP specific bulk accounting
# pgsql-voip
# For Exec-Program and Exec-Program-Wait
exec
# Filter attributes from the accounting response.
attr_filter.accounting_response
#
# See “Autz-Type Status-Server” for how this works.
#
# Acct-Type Status-Server {
#
# }
}
# Session database, used for checking Simultaneous-Use. Either the radutmp
# or rlm_sql module can handle this.
# The rlm_sql module is *much* faster
session {
#radutmp
#
# See “Simultaneous Use Checking Queries” in sql.conf
sql
}
# Post-Authentication
# Once we KNOW that the user has been authenticated, there are
# additional steps we can take.
post-auth {
# Get an address from the IP Pool.
# main_pool
#
# If you want to have a log of authentication replies,
# un-comment the following line, and the ‘detail reply_log’
# section, above.
# reply_log
#
# After authenticating the user, do another SQL query.
#
# See “Authentication Logging Queries” in sql.conf
sql
#
# Instead of sending the query to the SQL server,
# write it into a log file.
#
sql_log
#
# Un-comment the following if you have set
# ‘edir_account_policy_check = yes’ in the ldap module sub-section of
# the ‘modules’ section.
#
# ldap
And what do you get when you try
# radtest user user 127.0.0.1 0 testing123
?
and do you have anything inside radacct table ?
mysql> select * from radacct;
+———–+—————+———————————-+———-+———–+——-+————–+———–+—————–+———————+———————+—————–+—————+——————-+——————+—————–+——————+—————–+——————+——————–+————-+—————-+—————–+—————-+—————+———————-+
| radacctid | acctsessionid | acctuniqueid | username | groupname | realm | nasipaddress | nasportid | nasporttype | acctstarttime | acctstoptime | acctsessiontime | acctauthentic | connectinfo_start | connectinfo_stop | acctinputoctets | acctoutputoctets | calledstationid | callingstationid | acctterminatecause | servicetype | framedprotocol | framedipaddress | acctstartdelay | acctstopdelay | xascendsessionsvrkey |
+———–+—————+———————————-+———-+———–+——-+————–+———–+—————–+———————+———————+—————–+—————+——————-+——————+—————–+——————+—————–+——————+——————–+————-+—————-+—————–+—————-+—————+———————-+
| 1 | 00003388 | dc215167ba40aef32c7e1faa40fef119 | user | | | 10.169.33.11 | 13378 | Wireless-802.11 | 2011-12-08 14:38:05 | NULL | 0 | RADIUS | | | 0 | 0 | 0013.1a08.9340 | 001b.7770.9159 | | Framed-User | | | 0 | 0 | |
| 2 | 0000338A | f06202ad114e163cee3ad9e9a21730a1 | user | | | 10.169.33.11 | 13379 | Wireless-802.11 | 2011-12-08 14:52:53 | 2011-12-08 15:02:11 | 558 | RADIUS | | | 19451 | 1770 | 0013.1a08.9340 | 001b.7770.9159 | Lost-Carrier | Framed-User | | | 0 | 0 | |
| 3 | 0000338C | 045e9dad71213a032a5808ac431de1c4 | user | | | 10.169.33.11 | 13380 | Wireless-802.11 | 2011-12-08 15:02:12 | 2011-12-08 15:02:27 | 15 | RADIUS | | | 1691 | 731 | 0013.1a08.9340 | 001b.7770.9159 | Lost-Carrier | Framed-User | | | 0 | 0 | |
| 4 | 0000338E | 786f8da876f28a2c50b708d944b1643f | user |
freebsd# radtest user user localhost 0 12345
Sending Access-Request of id 163 to 127.0.0.1 port 1812
User-Name = “user”
User-Password = “user”
NAS-IP-Address = 192.168.20.200
NAS-Port = 0
Message-Authenticator = 0x00
rad_recv: Access-Accept packet from host 127.0.0.1 port 1812, id=163, length=20
freebsd#
Check your dialup.conf file inside sql/mysql
You should have uncommented
# Uncomment simul_count_query to enable simultaneous use checking
simul_count_query = “SELECT COUNT(*) \
FROM ${acct_table1} \
WHERE username = ‘%{SQL-User-Name}’ \
….
Post that query here in case it is already uncommented…
it was done!
can you post the query here…
And the radiusd -X output but only the relevant part …
At first thank for nice blog,
my testing reply below
Sending Access-Request of id 176 to 127.0.0.1 port 1812
User-Name = “test”
User-Password = “123”
NAS-IP-Address = 127.0.0.1
NAS-Port = 0
rad_recv: Access-Accept packet from host 127.0.0.1 port 1812, id=176, length=54
Ascend-Xmit-Rate = 524288
Ascend-Data-Rate = 131072
Framed-Pool = “internet”
how can i fixed below reply:
NAS-IP-Address = 192.168.1.10
AND
—
can u help me please how can i run pppoe + freeradius2+ mysql in Linux enterprise 5.5
using rpm for pppoe below :
rp-pppoe-3.5-32.1
ppp-2.4.4-2.el5
And
using rpm for freeradius2 below:
freeradius2-krb5-2.1.7-7.el5
freeradius2-perl-2.1.7-7.el5
freeradius2-mysql-2.1.7-7.el5
freeradius2-unixODBC-2.1.7-7.el5
freeradius2-ldap-2.1.7-7.el5
freeradius2-python-2.1.7-7.el5
freeradius2-postgresql-2.1.7-7.el5
freeradius2-2.1.7-7.el5
freeradius2-utils-2.1.7-7.el5
AND
using rpm for mysql below:
mysql-bench-5.0.77-4.el5_4.2
mysql-server-5.0.77-4.el5_4.2
mysql-test-5.0.77-4.el5_4.2
freeradius2-mysql-2.1.7-7.el5
mysql-5.0.77-4.el5_4.2
mysql-devel-5.0.77-4.el5_4.2
mysql-connector-odbc-3.51.26r1127-1.el5
I agree that blog is fine!!!
my radisud -X (the part for connection of secont user)
=============
rad_recv: Access-Request packet from host 10.169.33.11 port 1645, id=165, length=168
User-Name = “user”
Framed-MTU = 1400
Called-Station-Id = “0013.1a08.9340”
Calling-Station-Id = “001b.7770.9159”
Service-Type = Login-User
Message-Authenticator = 0x63a36c19356a73ecce742452dfab1595
EAP-Message = 0x020c00261900170301001ba202a3c6d1636e87a64e82638e24573e6333b359f013502bc5265b
NAS-Port-Type = Wireless-802.11
NAS-Port = 13651
State = 0x3156a9eb385ab02442063b3e8be26be4
NAS-IP-Address = 10.169.33.11
NAS-Identifier = “ap”
(23) # Executing section authorize from file /usr/local/etc/raddb/sites-enabled/default
(23) group authorize {
(23) – entering group authorize {…}
(23) [preprocess] = ok
(23) [chap] = noop
(23) [mschap] = noop
(23) [digest] = noop
(23) suffix : No ‘@’ in User-Name = “user”, looking up realm NULL
(23) suffix : No such realm “NULL”
(23) [suffix] = noop
(23) eap : EAP packet type response id 12 length 38
(23) eap : Continuing tunnel setup.
(23) [eap] = ok
(23) Found Auth-Type = ?
(23) # Executing group from file /usr/local/etc/raddb/sites-enabled/default
(23) group authenticate {
(23) – entering group authenticate {…}
(23) eap : Request found, released from the list
(23) eap : EAP/peap
(23) eap : processing type peap
(23) peap : processing EAP-TLS
(23) peap : eaptls_verify returned 7
(23) peap : Done initial handshake
(23) peap : eaptls_process returned 7
(23) peap : FR_TLS_OK
(23) peap : Session established. Decoding tunneled attributes.
(23) peap : Peap state send tlv success
(23) peap : Received EAP-TLV response.
(23) peap : Success
(23) peap : Using saved attributes from the original Access-Accept
User-Name = “user”
(23) eap : Freeing handler
(23) [eap] = ok
(23) Login OK: [user/] (from client 10.169.33.11/24 port 13651 cli 001b.7770.9159)
(23) # Executing section post-auth from file /usr/local/etc/raddb/sites-enabled/default
(23) group post-auth {
(23) – entering group post-auth {…}
(23) sql : expand: %{User-Name} -> user
(23) sql : sql_set_user escaped user –> ‘user’
(23) sql : expand: %{User-Password} ->
(23) sql : … expanding second conditional
(23) sql : expand: %{Chap-Password} ->
(23) sql : expand: INSERT INTO radpostauth (username, pass, reply, authdate) VALUES ( ‘%{SQL-User-Name}’, ‘%{%{User-Password}:-%{Chap-Password}}’, ‘%{reply:Packet-Type}’, ‘%S’) -> INSERT INTO radpostauth (username, pass, reply, authdate) VALUES ( ‘user’, ”, ‘Access-Accept’, ‘2011-12-14 13:57:54’)
rlm_sql (sql) in sql_postauth: query is INSERT INTO radpostauth (username, pass, reply, authdate) VALUES ( ‘user’, ”, ‘Access-Accept’, ‘2011-12-14 13:57:54’)
rlm_sql (sql): Reserved connection (4)
rlm_sql (sql): Released connection (4)
(23) [sql] = ok
(23) sql_log : Processing sql_log_postauth
(23) sql_log : expand: %{User-Name} -> user
(23) sql_log : expand: %{%{User-Name}:-DEFAULT} -> user
(23) sql_log : sql_set_user escaped user –> ‘user’
(23) sql_log : WARNING: Deprecated conditional expansion “:-“. See “man unlang” for details
(23) sql_log : … expanding second conditional
(23) sql_log : expand: Chap-Password -> Chap-Password
(23) sql_log : expand: INSERT INTO radpostauth (username, pass, reply, authdate) VALUES (‘%{User-Name}’, ‘%{User-Password:-Chap-Password}’, ‘%{reply:Packet-Type}’, ‘%S’); -> INSERT INTO radpostauth (username, pass, reply, authdate) VALUES (‘user’, ‘Chap-Password’, ‘Access-Accept’, ‘2011-12-14 13:57:54’);
(23) sql_log : expand: /usr/local/var/log/radius/radacct/sql-relay -> /usr/local/var/log/radius/radacct/sql-relay
(23) [sql_log] = ok
(23) [exec] = noop
(23) policy remove_reply_message_if_eap {
(23) – entering policy remove_reply_message_if_eap {…}
(23) ? if (reply:EAP-Message && reply:Reply-Message)
(23) ? Evaluating (reply:EAP-Message ) -> TRUE
(23) ? Evaluating (reply:Reply-Message) -> FALSE
(23) ? if (reply:EAP-Message && reply:Reply-Message) -> FALSE
(23) else else {
(23) – entering else else {…}
(23) [noop] = noop
(23) – else else returns noop
(23) – policy remove_reply_message_if_eap returns noop
Sending Access-Accept of id 165 to 10.169.33.11 port 1645
User-Name = “user”
MS-MPPE-Recv-Key = 0x41ee2c65cadadbda1e1b934aa4d1be2652955709153bc6554e79b9908498c5a0
MS-MPPE-Send-Key = 0x57bfc449af0486b315e3bdcc0808cec4d68b281e33ebd3e6a2c557fe1f06cd81
EAP-Message = 0x030c0004
Message-Authenticator = 0x00000000000000000000000000000000
(23) Finished request 23.
Waking up in 0.2 seconds.
rad_recv: Accounting-Request packet from host 10.169.33.11 port 1646, id=249, length=224
Acct-Session-Id = “000034BF”
Called-Station-Id = “0013.1a08.9340”
Calling-Station-Id = “001b.7770.9159”
Cisco-AVPair = “ssid=HAYATT”
Cisco-AVPair = “vlan-id=55”
Cisco-AVPair = “nas-location=unspecified”
User-Name = “user”
Cisco-AVPair = “connect-progress=Call Up”
Acct-Authentic = RADIUS
Acct-Status-Type = Start
NAS-Port-Type = Wireless-802.11
Cisco-NAS-Port = “13651”
NAS-Port = 13651
Service-Type = Framed-User
NAS-IP-Address = 10.169.33.11
Acct-Delay-Time = 0
(24) # Executing section preacct from file /usr/local/etc/raddb/sites-enabled/default
(24) group preacct {
(24) – entering group preacct {…}
(24) [preprocess] = ok
(24) policy acct_unique {
(24) – entering policy acct_unique {…}
(24) ? if (“%{string:Class}” =~ /ai:([0-9a-f]{32})/i)
(24) expand: %{string:Class} ->
(24) ? Evaluating (“%{string:Class}” =~ /ai:([0-9a-f]{32})/i) -> FALSE
(24) ? if (“%{string:Class}” =~ /ai:([0-9a-f]{32})/i) -> FALSE
(24) else else {
(24) – entering else else {…}
(24) update request {
(24) expand: %{User-Name}%{Acct-Session-ID}%{NAS-IP-Address}%{NAS-Port-ID:}%{NAS-Port} -> user000034BF10.169.33.1113651
(24) expand: %{md5:%{User-Name}%{Acct-Session-ID}%{NAS-IP-Address}%{NAS-Port-ID:}%{NAS-Port}} -> 8d18fcff10a1dcca6418fe194d60ec0c
(24) } # update request = ok
(24) – else else returns ok
(24) – policy acct_unique returns ok
(24) suffix : No ‘@’ in User-Name = “user”, looking up realm NULL
(24) suffix : No such realm “NULL”
(24) [suffix] = noop
(24) [files] = noop
(24) # Executing section accounting from file /usr/local/etc/raddb/sites-enabled/default
(24) group accounting {
(24) – entering group accounting {…}
(24) detail : expand: %{Packet-Src-IP-Address} -> 10.169.33.11
(24) detail : expand: /usr/local/var/log/radius/radacct/%{%{Packet-Src-IP-Address}:-%{Packet-Src-IPv6-Address}}/detail-%Y%m%d -> /usr/local/var/log/radius/radacct/10.169.33.11/detail-20111214
(24) detail : /usr/local/var/log/radius/radacct/%{%{Packet-Src-IP-Address}:-%{Packet-Src-IPv6-Address}}/detail-%Y%m%d expands to /usr/local/var/log/radius/radacct/10.169.33.11/detail-20111214
(24) detail : expand: %t -> Wed Dec 14 13:57:54 2011
(24) [detail] = ok
(24) [unix] = ok
(24) sql : expand: %{User-Name} -> user
(24) sql : sql_set_user escaped user –> ‘user’
(24) sql : expand: %{Acct-Delay-Time} -> 0
(24) sql : expand: INSERT INTO radacct (acctsessionid, acctuniqueid, username, realm, nasipaddress, nasportid, nasporttype, acctstarttime, acctstoptime, acctsessiontime, acctauthentic, connectinfo_start, connectinfo_stop, acctinputoctets, acctoutputoctets, calledstationid, callingstationid, acctterminatecause, servicetype, framedprotocol, framedipaddress, acctstartdelay, acctstopdelay, xascendsessionsvrkey) VALUES (‘%{Acct-Session-Id}’, ‘%{Acct-Unique-Session-Id}’, ‘%{SQL-User-Name}’, ‘%{Realm}’, ‘%{NAS-IP-Address}’, ‘%{NAS-Port}’, ‘%{NAS-Port-Type}’, ‘%S’, NULL, ‘0’, ‘%{Acct-Authentic}’, ‘%{Connect-Info}’, ”, ‘0’, ‘0’, ‘%{Called-Station-Id}’, ‘%{Calling-Station-Id}’, ”, ‘%{Service-Type}’, ‘%{Framed-Protocol}’, ‘%{Framed-IP-Address}’, ‘%{%{Acct-Delay-Time}:-0}’, ‘0’, ‘%{X-Ascend-Session-Svr-Key}’) -> INSERT INTO radacct (acctsessionid, acctuniqueid, username, realm, nasipaddress, nasportid, nasporttype, acctstarttime, acctstoptime, acctsessiontime, acctauthentic, connectinfo_start, connectinfo_stop, acctinputoctets, acctoutputoctets, calledstationid, callingstationid, acctterminatecause, servicetype, framedprotocol, framedipaddress, acctstartdelay, acctstopdelay, xascendsessionsvrkey) VALUES (‘000034BF’, ‘8d18fcff10a1dcca6418fe194d60ec0c’, ‘user’, ”, ‘10.169.33.11’, ‘13651’, ‘Wireless-802.11’, ‘2011-12-14 13:57:54’, NULL, ‘0’, ‘RADIUS’, ”, ”, ‘0’, ‘0’, ‘0013.1a08.9340’, ‘001b.7770.9159’, ”, ‘Framed-User’, ”, ”, ‘0’, ‘0’, ”)
rlm_sql (sql): Reserved connection (4)
rlm_sql (sql): Released connection (4)
(24) [sql] = ok
(24) sql_log : Processing sql_log_accounting
(24) sql_log : expand: %{User-Name} -> user
(24) sql_log : expand: %{%{User-Name}:-DEFAULT} -> user
(24) sql_log : sql_set_user escaped user –> ‘user’
(24) sql_log : expand: INSERT INTO radacct (AcctSessionId, UserName, NASIPAddress, FramedIPAddress, AcctStartTime, AcctStopTime, AcctSessionTime, AcctTerminateCause) VALUES (‘%{Acct-Session-Id}’, ‘%{User-Name}’, ‘%{NAS-IP-Address}’, ‘%{Framed-IP-Address}’, ‘%S’, ‘0’, ‘0’, ”); -> INSERT INTO radacct (AcctSessionId, UserName, NASIPAddress, FramedIPAddress, AcctStartTime, AcctStopTime, AcctSessionTime, AcctTerminateCause) VALUES (‘000034BF’, ‘user’, ‘10.169.33.11’, ”, ‘2011-12-14 13:57:54’, ‘0’, ‘0’, ”);
(24) sql_log : expand: /usr/local/var/log/radius/radacct/sql-relay -> /usr/local/var/log/radius/radacct/sql-relay
(24) [sql_log] = ok
(24) [exec] = noop
(24) attr_filter.accounting_response : expand: %{User-Name} -> user
(24) attr_filter.accounting_response : Matched entry DEFAULT at line 12
(24) [attr_filter.accounting_response] = updated
Sending Accounting-Response of id 249 to 10.169.33.11 port 1646
====================
Dear all,
please help me ,
Now how can i connected pppoe+freeradius2+mysql
BR
Nishu
I wrote 4 posts about freeradius and if you read them carefully you can do it yourself…
Other option is to pay someone to do it for you…
Dear admin ,
Thanks for my reply i am following your document step by step all 4 posts blog,
I am user Linux enterprise 5.5 server.
my using rpm below for freeradius2 :
———————————————–
freeradius2-krb5-2.1.7-7.el5
freeradius2-perl-2.1.7-7.el5
freeradius2-mysql-2.1.7-7.el5
freeradius2-unixODBC-2.1.7-7.el5
freeradius2-ldap-2.1.7-7.el5
freeradius2-python-2.1.7-7.el5
freeradius2-postgresql-2.1.7-7.el5
freeradius2-2.1.7-7.el5
freeradius2-utils-2.1.7-7.el5
And for mysql using below rpm :
using rpm for mysql below:
mysql-bench-5.0.77-4.el5_4.2
mysql-server-5.0.77-4.el5_4.2
mysql-test-5.0.77-4.el5_4.2
freeradius2-mysql-2.1.7-7.el5
mysql-5.0.77-4.el5_4.2
mysql-devel-5.0.77-4.el5_4.2
mysql-connector-odbc-3.51.26r1127-1.el5
also
using rpm for pppoe below :
rp-pppoe-3.5-32.1
ppp-2.4.4-2.el5
My reply on following by your blog below:
[root@localhost /]# radtest test 123 127.0.0.1 0 testing123
Sending Access-Request of id 94 to 127.0.0.1 port 1812
User-Name = “test”
User-Password = “123”
NAS-IP-Address = 127.0.0.1
NAS-Port = 0
rad_recv: Access-Accept packet from host 127.0.0.1 port 1812, id=94, length=54
Ascend-Xmit-Rate = 524288
Ascend-Data-Rate = 131072
Framed-Pool = “internet”
that is ok or something i missing if u want i will show you my radiusd -X
my server raddb location is /etc/raddb/
radiusd+mysql working but how can i working pppoe with radiusd+mysql.
my problem is i can’t connected pppoe + radiusd + mysql,
if you can please help me i am waiting for your kind reply its very important
for me.
any information u need to know ,please inform me.
BR
nishu
Dear admin ,
if u can please help me ASAP
BR
nishu
I wouldn’t use rp-pppoe when you can buy Mikrotik for less then 500USD and it works very good.
For your case, check this link
http://blog.webdir.bg/linux-pppoe-server-with-radius-suuport/
Dear admin ,
Thank for your kind reply for me .
i will trying your link and let u know the update.
BR
Nishu
Dear admin ,
it didn’t working in Linux enterprise 5.5 server ,if u have any other link about my problem please post the link
BR
nishu
Dear admin ,
i have follow your blog 4 step and now i have install Mikrotik anther PC .i don’t understood how can i connect linux + Mikrotik ,if you can please help setup mikrotik for AAA with pppoe
BR
Nishu
Check this blog post
http://www.serveradminblog.com/2012/01/freeradius-install-howto-5-mikrotik-settings/
Dear admin,
I follow this tutorial for freeradius + mysql server for external authentication for my mikrotik router. And I don’t understand, if I try to connect with my nas client (mikrotik), always no response. help me please. (sory for my english) 🙂
Go back and check all config files… Check is radius started…
Great Blog ! Please more freeradius tutorials like
– simultaniouse-use with SNMP session alive check on the NAS.
– restrict users to monthly input+outputoctets via mysql
– List of usefull AV-Pairs and where to get vendor specific AV-Pair information.
( In my case Cisco WCS url-redirects , only find TACACS+ Infromation.)
These Information are hard to find and would be GREAT ! I’m from Germany and there are no Courses i can take about these Information, even if i would pay for it.
hi this is my users file and im strugguling using this in Mysql table ..its working fine in my users file; its a one time password , im using it to authenticate user but i dont really know wich table or wich attribute to use in mysql database
any help is wellcome
serveur:/etc/raddb# cat /etc/raddb/users
DEFAULT Auth-Type = External
Exec-Program-Wait = “/etc/raddb/otpverify.sh ‘%{User-Name}’ ‘%{User-Password}’ ‘%{reply:Secret}’ ‘%{reply:Pin}’ ‘%{reply:Offset}'”,
Fall-Through = Yes
karim
Secret = e37629f6d057dcc5,
PIN = 1234,
Offset = 0
for check attributes you should use radcheck and for reply radreply table… Check examples above
HI admin, what if I have 2 groups with different priority. Example would be user1 (with priority 1 & group1) would be able to access Server1 and user2 (with priority2 & group2) would be able to access Server1 & Server2. How can I do that in the db and radius configuration?
Like:
user1 ->access Server1 only
user2 -> access Server1 & Server2
Hi admin.
Please, I want to setup freeradius to auth windows wifi clients on a openldap + samba 3 domain. I need pre-auth via eap-tls (certificates) the stations, but the WIndows place the string “host/’ before the CN defined on certificate placed on local machine certificate store, then the search on ldap fails. How process correctly this auth request? The client certificate works fine. Could you indicate some guide for help me?
Thanks
Hi
I’m not sure but maybe unlang and attribute rewrite option can help.
http://freeradius.org/radiusd/man/rlm_attr_rewrite.html
http://freeradius.org/radiusd/man/unlang.html
The other option can be perl script (Check rlm_perl and exec modules)
hi
ihave freeradius server running in ubuntu
i want to use cisco access point to relay connection to freeradius server
the problem is that the server reject users
i listed the access point in clients.conf and nas table and iam testing with laptop using windows7 os
i am beginner
Run the server in debug. mode and check the output.
rad_recv: Access-Request packet from host 192.168.2.1 port 1024, id=19, length=146
User-Name = “sqltest”
NAS-IP-Address = 192.168.2.1
NAS-Port = 0
Called-Station-Id = “*************”
Calling-Station-Id = “********************”
Framed-MTU = 1400
NAS-Port-Type = Wireless-802.11
EAP-Message = 0x0204001119800000000715030100020230
State = 0xc862adf4ca66b4ed86a78d75f615334a
Message-Authenticator = 0xec44d346a121c0f5c0818cf862b898dd
# Executing section authorize from file /etc/freeradius/sites-enabled/default
+- entering group authorize {…}
++[preprocess] returns ok
++[chap] returns noop
++[mschap] returns noop
++[digest] returns noop
[suffix] No ‘@’ in User-Name = “sqltest”, looking up realm NULL
[suffix] No such realm “NULL”
++[suffix] returns noop
[eap] EAP packet type response id 4 length 17
[eap] Continuing tunnel setup.
++[eap] returns ok
Found Auth-Type = EAP
# Executing group from file /etc/freeradius/sites-enabled/default
+- entering group authenticate {…}
rlm_eap: No EAP session matching the State variable.
[eap] Either EAP-request timed out OR EAP-response to an unknown EAP-request
[eap] Failed in handler
++[eap] returns invalid
Failed to authenticate the user.
Using Post-Auth-Type Reject
# Executing group from file /etc/freeradius/sites-enabled/default
+- entering group REJECT {…}
[attr_filter.access_reject] expand: %{User-Name} -> sqltest
attr_filter: Matched entry DEFAULT at line 11
hi dear admin
how automatically freeradius disconnect user when use over time or octets?
In Expiration field, we have to use the := operator in MySQL.
For me it works with “==” and date format “September 11 2009 00:00:00”
Tested with Mikrotik only
i have smartphone + win 8 authentication with freeradius 2.x but windows 7 + windows xp can’t not authentication with freeradius 2.x.
Thanks!
You think I have some kind of crystal ball? Have you ever heard anything about logs, debugging, etc ?
when i use win 7, the error:
Found Auth-Type = EAP
# Executing group from file /etc/raddb/sites-enabled/default
+- entering group authenticate {…}
[eap] Request found, released from the list
[eap] EAP/peap
[eap] processing type peap
[peap] processing EAP-TLS
TLS Length 7
[peap] Length Included
[peap] eaptls_verify returned 11
[peap] <<< TLS 1.0 Alert [length 0002], fatal unknown_ca
TLS Alert read:fatal:unknown CA
TLS_accept: failed in SSLv3 read client certificate A
rlm_eap: SSL error error:14094418:SSL routines:SSL3_READ_BYTES:tlsv1 alert unknown ca
SSL: SSL_read failed inside of TLS (-1), TLS session fails.
TLS receive handshake failed during operation
[peap] eaptls_process returned 4
[peap] EAPTLS_OTHERS
[eap] Handler failed in EAP/peap
[eap] Failed in EAP select
++[eap] returns invalid
Failed to authenticate the user.
On win 8 and smartphone android not use certified but on win 8 and android smartphones have been certified.
Thanks!
Seems like similar problem like on this link http://freeradius.1045715.n5.nabble.com/windows-users-having-trouble-authenticating-td2783717.html
Set EAP to TLS and try again
Hi. I’m fix error. windows 7 not support eap-ttls. Install secureW2 software on win7. Thanks you rep!
thanks for this blog
i need to ask
if my database oracle
i can replace authentication , accounting query with pl/sql block in dialup.conf??
if possible ..how
thanks
Nice blog, one question how can I bind MAC id’s
Hi, admin.
My server is able to authenticate the user from my database but i found that the radacct table is empty. It do not update any info when user log in. I have checked the configuration in /sites-enable/default, sql is uncommented in accounting{}. And i have no idea how to fix this problem as it cause me unable to use Simultaneous-Use and Session-Timeout.
Please help me . Thank you
Check the NAS (radius accounting should be turned on). The 5min. intervals will be Ok.
If you already checked this, run the server in debug mode and check the accounting records. You’ll be able to see the complete accounting process.
Controlling simmultaneous use on Mikrotik you must use PORT-LIMIT attribute besides off simultaneous-use…
Session-Timeou is not working. I put Silmultaneous-Use in radgroupreply. I use := operator. Someone can help-me?
– Silmultaneous-Use goes in check tables,
– Session-Timeout in reply tables
Both with “:=”
Hello,
Hi,
This is what I send;
root@be2:/etc/freeradius/3.0/sites-enabled# radtest testuser testpassword 127.0.0.1 0 secret Sent Access-Request Id 28 from 0.0.0.0:42886 to 127.0.0.1:1812 length 78
User-Name = “testuser”
User-Password = “testpassword”
NAS-IP-Address = 192.168.0.25
NAS-Port = 0
Message-Authenticator = 0x00
Cleartext-Password = “testpassword”
Received Access-Reject Id 28 from 127.0.0.1:1812 to 0.0.0.0:0 length 20
(0) -: Expected Access-Accept got Access-Reject
What I noticed is that based on this tutorial, which I followed now .
https://www.serveradminblog.com/2011/12/freeradius-install-howto-4-populating-tables/
I should have gotten this:
[root@ns2 raddb]# radtest testuser testpassword 127.0.0.1 0 testing123 Sending Access-Request of id 228 to 127.0.0.1 port 1812
User-Name = “testuser”
User-Password = “testpassword”
NAS-IP-Address = 192.168.0.10
NAS-Port = 0
Message-Authenticator = 0x00000000000000000000000000000000
rad_recv: Access-Accept packet from host 127.0.0.1 port 1812, id=228, length=54
Ascend-Xmit-Rate = 524288
Ascend-Data-Rate = 131072
Framed-Pool = “internet”
So, in the tutorial, Cleartext-Password = “testpassword” does not show up. Can it be the error? Does anybody know how to fix it?
Thanks
BR
Tutorial was written 7 years ago (for FR 2.x) and yes, it seems that “Cleartext-Password = “testpassword”” is something new for 3.x branch.
Just tested the command and it works fine for me.
radiusd -v
radiusd: FreeRADIUS Version 3.0.17
mysql> select * from radcheck;
+—-+———-+——————+—-+———————————-+
| id | username | attribute | op | value |
+—-+———-+——————+—-+———————————-+
| 8 | testuser | NT-Password | := | NT_PASSWORD_HASH |
radtest -x testuser CORRECT_PASS 127.0.0.1 0 testing123
Sent Access-Request Id 40 from 0.0.0.0:36959 to 127.0.0.1:1812 length 77
User-Name = “testuser”
User-Password = “CORRECT_PASS”
NAS-IP-Address = 127.0.0.1
NAS-Port = 0
Message-Authenticator = 0x00
Cleartext-Password = “CORRECT_PASS”
Received Access-Accept Id 40 from 127.0.0.1:1812 to 127.0.0.1:36959 length 20
radtest -x testuser WRONG_PASS 127.0.0.1 0 testing123
Sent Access-Request Id 37 from 0.0.0.0:51385 to 127.0.0.1:1812 length 77
User-Name = “testuser”
User-Password = “WRONG_PASS”
NAS-IP-Address = 127.0.0.1
NAS-Port = 0
Message-Authenticator = 0x00
Cleartext-Password = “WRONG_PASS”
Received Access-Reject Id 37 from 127.0.0.1:1812 to 127.0.0.1:51385 length 20
(0) -: Expected Access-Accept got Access-Reject
I’m not sure why do you have a problem but please check that FR is connected to database. Also, please check the nas secret since testing123 is the default one for localhost